Synchronized User Rights Management
Managing systems users can be a challenging aspect of implementing a GPS tracking and telematics system. Employees routinely come and go and the IT department or the GPS program manager is constantly struggling to keep up with employee changes. Additionally, this process may take time which leaves a window of opportunity for a disgruntled employee to access the system.
Integrated user management works from existing systems to automatically manage users in the GPS fleet management portal. Changes made in your normal employee management system are reflected in the portal when user access rights are checked between the systems. When you block an employee on your system, it immediately blocks the user on the Fleetistics portal.
Single Sign On (SSO) TechNet Magazine
Azure AD is the latest “flavor” of Active Directory. Azure AD utilizes cloud technology thus avoiding the server in the closet just for ADFS. Read more here.
The OAuth 2.0 is the industry protocol for authorization. It allows a user to grant limited access to its protected resources. Designed to work specifically with Hypertext Transfer Protocol (HTTP), OAuth separates the role of the client from the resource owner. The client requests access to the resources controlled by the resource owner and hosted by the resource server. The resource server issues access tokens with the approval of the resource owner. The client uses the access tokens to access the protected resources hosted by the resource server.
Active Directory Federation Services
ADFS Best Practices
Standardization – Your organization may have a large set of business and legal requirements for setting up federation partners, but the ADFS technical requirements are fairly simple. Whether your organization will be functioning in the account or resource partner role, you’ll need to agree with each partner on the actual names for the claims that will be exchanged across organizations. If you are a resource partner with numerous account partners, it may be fairly easy to develop a standard set of mappings and ask your account partners to conform as part of the partnership. As a resource partner, you must also make sure you obtain each account partner’s token-signing certificate, which must be configured when creating the partner in the ADFS trust policy.
Automation – For organizations with complex workflows and business processes and high partner churn, the ADFS OM API offers an alternative to the manual configuration process. The OM API allows programmatic access to trust policy construction and editing. Organizations with existing custom tools for handling business processes can integrate ADFS trust policy editing into the partnering process tools directly. As partner volume and churn increase, this can also be preferable to allow for some automation as well as extended partner-analysis functionality.
Matt Steele – is a Program Manager on the Active Directory Federation Services team at Microsoft. Matt is currently working on ADFS product integrations and supporting the design of future identity and access technologies. View
?2008 Microsoft Corporation and CMP Media, LLC. All rights reserved; reproduction in part or in whole without permission is prohibited.

Azure AD or ADFS Setup
ADFS is free if you are using Active Directory 2008 or newer. It is an “add-on” which enables access to your network from outside your network. Don’t worry, ADFS is secure and a standard Microsoft service used by thousands of large companies
Secure Process
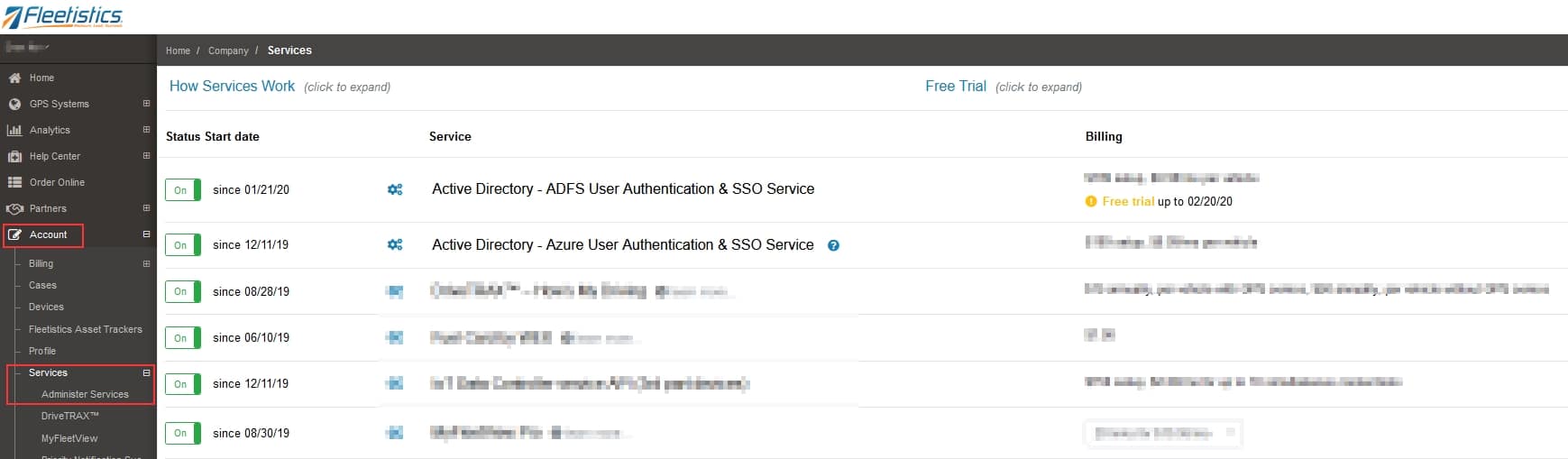
Fleetistics will provide a set of groups which all users are assigned to in the customers Active Directory (AD). AD then passes this information to ADFS which acts as the secured gateway to external access. When a user attempts to login to the MyFleetistics portal, the request generates a token which is sent to the customers ADFS for authentication. Upon authentication, a token is returned which is matched to the request and the user is able to login with the groups access rights assigned.
Industry First AD Integration
Fleetistics is proud to be the first in the industry to offer user management through integration of Active Directory. Through the use of Active Directory groups, user access to features of the MyFleetistics portal can be centrally managed using the same familiar tools and processes already in place within your organization.
Contact Fleetistics
Ask about testing a fleet monitoring service